After creating an email account in CyberPanel some users would like to configure their email accounts to third party email clients such as Outlook or Thunderbird.
Both these clients have auto-discover functionality, this functionality will try to automatically configure your email settings so that end-user won’t have to do anything. For example, if on Thunderbird I configure:
- User: [email protected]
- Password:
Thunderbird may suggest the following settings:
Server hostname: mail.cyberpanel.net
IMAP Port: 143
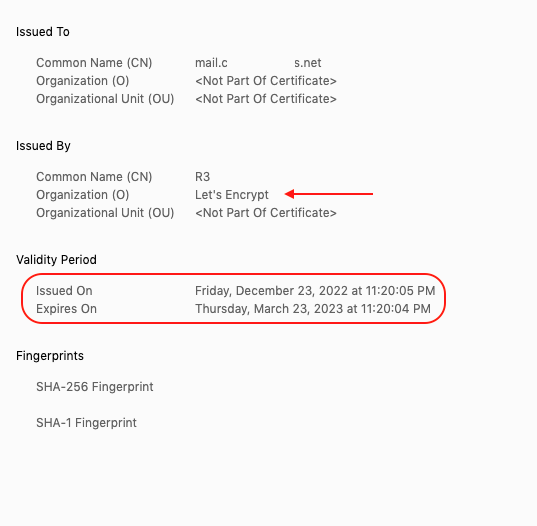
Now Thunderbird will be looking for a valid SSL for mail.cyberpanel.net and if valid SSL is not offered by the server you will get a self-signed SSL error.
How to resolve Self-signed SSL Error
After version v1.9.4 of CyberPanel, upon website creation, CyberPanel will create mail.domain.com as a child domain to while creating a website and also issue SSL for it. Then CyberPanel will add edit /etc/dovecot/dovecot.conf and add the following to the file:
local_name mail.domain.com {
ssl_cert = </etc/letsencrypt/live/mail.domain.com/fullchain.pem
ssl_key = </etc/letsencrypt/live/mail.domain.com/privkey.pem
}
and then restart dovecot service using systemctl restart dovecot. This way there will be no SSL errors on either Outlook or Thunderbird.
Manually setting this up
Let say you are on some of the old versions of CyberPanel or you have already created a website before upgrading to v1.9.4. You can go ahead and create mail.domain.com as a child-domain to your master domain also make sure to issue SSL for this domain.
Step 1: Open the file /etc/postfix/main.cf using any editor
sudo nano /etc/postfix/main.cf
Step 2: Comment the first two lines in that file by adding an # sign at the beginning.
# smtpd_tls_cert_file = /etc/pki/dovecot/certs/dovecot.pem
# smtpd_tls_key_file = /etc/pki/dovecot/private/dovecot.pem
Step 3: Add the following lines after changing. Remember to replace YourPrimaryMailServerDomain with the your own domain.
# provide the primary certificate for the server, to be used for outgoing connections
smtpd_tls_chain_files =
/etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/privkey.pem,
/etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/fullchain.pem
Step 4: In order to support SNI you need to add the following lines at the end
# provide the map to be used when SNI support is enabled
tls_server_sni_maps = hash:/etc/postfix/vmail_ssl.map
After all the above steps your files should look like this
# smtpd_tls_cert_file = /etc/pki/dovecot/certs/dovecot.pem
# smtpd_tls_key_file = /etc/pki/dovecot/private/dovecot.pem
# provide the primary certificate for the server, to be used for outgoing connections
smtpd_tls_chain_files =
/etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/privkey.pem,
/etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/fullchain.pem
# provide the map to be used when SNI support is enabled
tls_server_sni_maps = hash:/etc/postfix/vmail_ssl.map
Step 5: Create a new file in /etc/postfix with the name of vmail_ssl.map
sudo touch /etc/postfix/vmail_ssl.map
Step 6: Edit the file to add your domain’s SSL certificates to the list like this
mail.yourprimarymailserverdomain.com
/etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/privkey.pem
/etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/fullchain.pem
Step 7 (Optional): If you have more than one domain to be supported add all of them one per line. The resulting file should look like this
# Compile with postmap -F hash:/etc/postfix/vmail_ssl.map when updating
# One host per line
mail.yourprimarymailserverdomain.com /etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/privkey.pem /etc/letsencrypt/live/mail.yourprimarymailserverdomain.com/fullchain.pem
mail.yoursecondarymailserverdomain.com /etc/letsencrypt/live/mail.yoursecondarymailserverdomain.com/privkey.pem /etc/letsencrypt/live/mail.yoursecondarymailserverdomain.com/fullchain.pem
# add more domains with keys and certs as needed
Step 8: Open /etc/dovecot/dovecot.conf
sudo nano /etc/dovecot/dovecot.conf
Step 9: Append the following to the end of the file, replace domain.com with your own domain
local_name mail.domain.com {
ssl_cert = </etc/letsencrypt/live/mail.domain.com/fullchain.pem
ssl_key = </etc/letsencrypt/live/mail.domain.com/privkey.pem
}
Step 10: Re-compile postmap with SNI using the following command
postmap -F hash:/etc/postfix/vmail_ssl.map
Step 11: Restart Postfix.
systemctl restart postfix
Step 12: Restart Dovecot
systemctl restart dovecot
Connect again using a mail client and you should not see the error.