Hello!
After installing CyberPanel there are somethings that you don’t want to do for having a smooth experience.
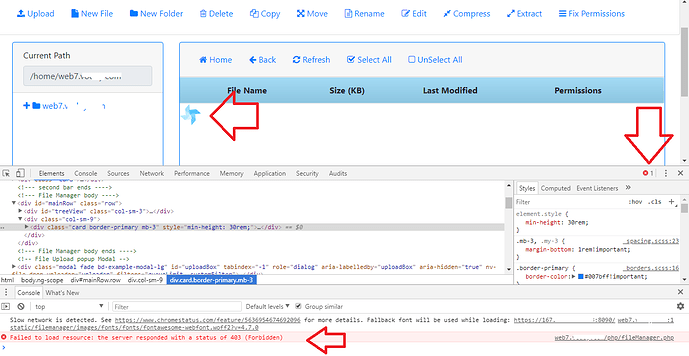
Don’t upload files via SFTP
Note: Don’t use SFTP as root to upload files, you can use website level user to upload files via sftp, more details here.
When you upload files via sftp they are owned by root, and CyberPanel runs each account through its own user, so once you have uploaded content via root, you might start getting permissions errors. More details can be found here.
Even though file manager now has one-click fix permission button to get rid of this issue, but this is still not a recommended way to upload content.
The recommended way is to use File Manager and FTP. They both use the same user as which scripts are executed for a particular site.
Changing MySQL Ports
If you want to change MySQL port, kindly update following part of a settings file.
The settings file is located at /usr/local/CyberCP/CyberCP/settings.py (Update the port part)
DATABASES = {
'default': {
'ENGINE': 'django.db.backends.mysql',
'NAME': 'cyberpanel',
'USER': 'cyberpanel',
'PASSWORD': 'cyberpanel',
'HOST': 'localhost',
'PORT':''
},
'rootdb': {
'ENGINE': 'django.db.backends.mysql',
'NAME': 'mysql',
'USER': 'root',
'PASSWORD': 'cyberpanel',
'HOST': 'localhost',
'PORT': '',
}
}
Once done, run
systemctl restart lscpd
MYSQL Password
If you change MySQL root password also update this file with updated password:
/etc/cyberpanel/mysqlPassword
Then you also need to update root password in settings file /usr/local/CyberCP/CyberCP/settings.py. Insert new password at new root password here
'rootdb': {
'ENGINE': 'django.db.backends.mysql',
'NAME': 'mysql',
'USER': 'root',
'PASSWORD': 'new root password here',
'HOST': 'localhost',
'PORT': '',
}
}
Finally also update root password in /home/cyberpanel/.my.cnf. If this file does not exist, you can skip.
After doing all these steps, make sure to run systemctl restart lscpd
This article is still a work in progress.