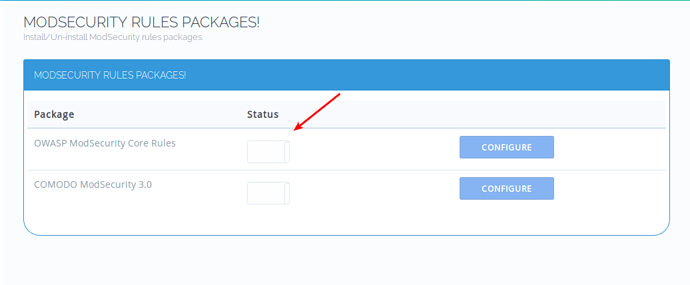
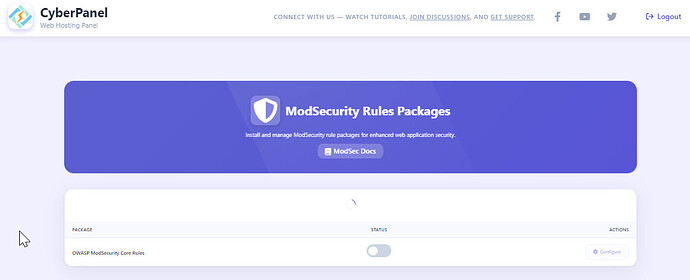
Starting version 1.6.2 stable you can now enable OWASP and Comodo Mod Security rules via one click.
Navigate to → https://:8090/firewall/modSecRulesPacks
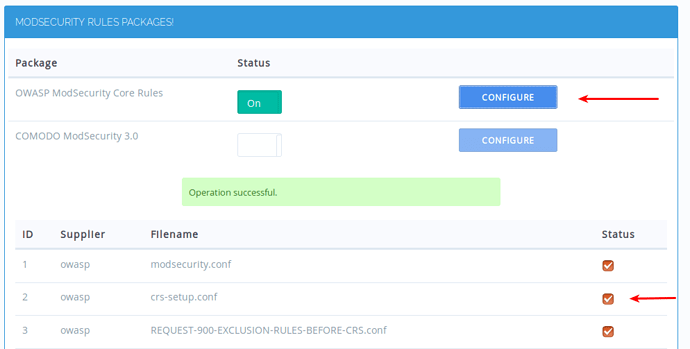
Click the switch and it will turn on OWASP Rules, to verify if OWASP rules are installed successfully, open:
http://example.com/?a=b AND 1=1
You should get 403 Forbidden error, you can also see your ModSecurity Audit logs:
ModSecurity: Warning. detected SQLi using libinjection. [file "/usr/local/lsws/conf/modsec/owasp/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf"] [line "17"] [id "942100"] [rev "1"] [msg "SQL Injection Attack Detected via libinjection"] [data "Matched Data: found within ARGS:a: b AND 1=1"] [severity "2"] [ver "OWASP_CRS/3.0.0"] [maturity "1"] [accuracy "8"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-sqli"] [tag "OWASP_CRS/WEB_ATTACK/SQL_INJECTION"] [tag "WASCTC/WASC-19"] [tag "OWASP_TOP_10/A1"] [tag "OWASP_AppSensor/CIE1"] [tag "PCI/6.5.2"] [hostname "dev.cyberpanel.net"] [uri "/"] [unique_id "152317238285.808317"] [ref "v8,9t:utf8toUnicode,t:urlDecodeUni,t:removeNulls,t:removeComments"]
ModSecurity: Access denied with code 403 (phase 2). Matched "Operator `Ge' with parameter `5' against variable `TX:ANOMALY_SCORE' (Value: `5' ) [file "/usr/local/lsws/conf/modsec/owasp/rules/REQUEST-949-BLOCKING-EVALUATION.conf"] [line "36"] [id "949110"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Score: 5)"] [data ""] [severity "2"] [ver ""] [maturity "0"] [accuracy "0"] [tag "application-multi"] [tag "language-multi"] [tag "platform-multi"] [tag "attack-generic"] [hostname "dev.cyberpanel.net"] [uri "/"] [unique_id "152317238285.808317"] [ref ""]
ModSecurity: Warning. Matched "Operator `Ge' with parameter `5' against variable `TX:INBOUND_ANOMALY_SCORE' (Value: `5' ) [file "/usr/local/lsws/conf/modsec/owasp/rules/RESPONSE-980-CORRELATION.conf"] [line "61"] [id "980130"] [rev ""] [msg "Inbound Anomaly Score Exceeded (Total Inbound Score: 5 - SQLI=5,XSS=0,RFI=0,LFI=0,RCE=0,PHPI=0,HTTP=0,SESS=0): SQL Injection Attack Detected via libinjection'"] [data ""] [severity "0"] [ver ""] [maturity "0"] [accuracy "0"] [tag "event-correlation"] [hostname "dev.cyberpanel.net"] [uri "/"] [unique_id "152317238285.808317"] [ref ""]
You can notice that rule from REQUEST-949-BLOCKING-EVALUATION.conf is triggered if you disable this file, you will not be getting 403 error.
Disable Rule Files
Once OWASP or Comodo rules are enabled you can also enable or disable individual rule files.