Any idea how to prevent user.ini from being shared ?
Thanks.
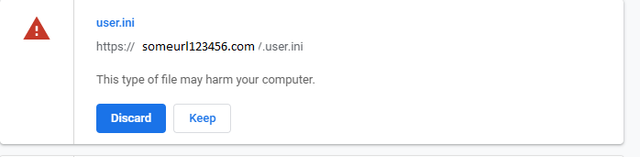
Any idea how to prevent user.ini from being shared ?URL: https://privateurl.com/.user.ini
Details: https://privateurl.com/.user.ini is publicly accessible and may expose source code or sensitive information about your site. Files such as this one are commonly checked for by scanners and should be made inaccessible. Alternately, some can be removed if you are certain your site does not need them. Sites using the nginx web server may need manual configuration changes to protect such files. Learn more
Thanks.
Publicly accessible config, backup, or log file found
This result shows files that may contain sensitive information that can be served by the web server. This may be backup copies of files, like a copy of wp-config.php under another name, log files, or configuration files.
Example scan result
Publicly accessible config, backup, or log file found: .user.ini
http://example.com/.user.ini is publicly accessible and may expose sensitive information about your site or allow administrative functions to be performed by anyone. Files such as this one are commonly checked for by both attackers and scanners such as WPScan and should be made inaccessible. Alternately, some can be removed if you are certain your site does not need them. Sites using the nginx web server may need manual configuration changes to protect such files.
Resolution
If you know that the file is not needed by your site, you can simply remove the file. This is often the case with files like “wp-config.bak”, which may be a backup copy of your wp-config.php. Do not remove files like “.user.ini” that may be required for your site to work properly.
If in doubt, the scan result includes the option to “Hide this file in .htaccess”, which will add a section to your .htaccess file to prevent Apache from serving this file, if you leave the file in place. This is recommended for .user.ini and similar files. You can run another scan after making the change, to make sure your server correctly blocks public access.
If you need to manually add the htaccess code, this should work for apache 2.2 and 2.4:
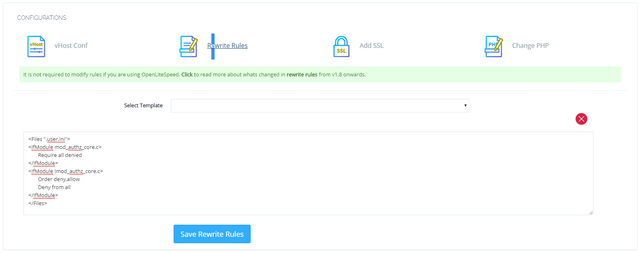
<Files “.user.ini”>
Require all denied
<IfModule !mod_authz_core.c>
Order deny,allow
Deny from all
If your site uses the NGINX web server, then you or your host may need to configure NGINX to block access to the file, whether NGINX is set up as a reverse proxy in front of Apache or if NGINX handles all requests directly. The method of blocking these files in NGINX varies depending on your current configuration, but one simple example is placing a “location” block like this, in the same file as your other “location” blocks:
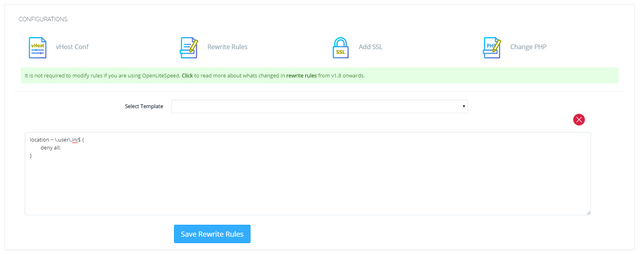
location ~ \.user\.ini$ {
deny all;
}
Make sure to restart NGINX or reload its config after making any changes to its config files, and then check that the .user.ini file is no longer visible in a web browser.
Is this correct htaccess on cyberpanel.
<Files “.user.ini”>
Require all denied
<IfModule !mod_authz_core.c>
Order deny,allow
Deny from all
Is this correct htaccess on cyberpanel. P Files ".user.ini" IfModule mod_authz_core.c Require all denied /IfModule IfModule !mod_authz_core.c Order deny,allow Deny from all /IfModule /Files /blockquote
please check this
https://openlitespeed.org/kb/access-control/
the simplest way is to use rewrite rule
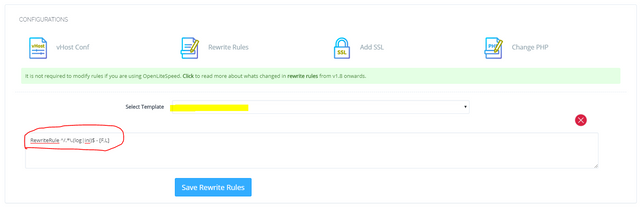
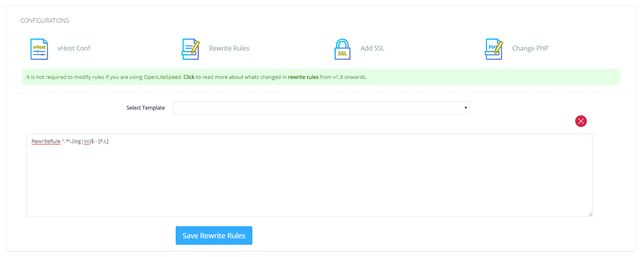
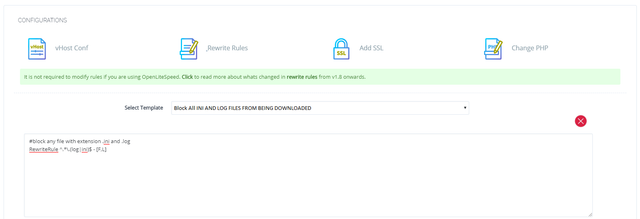
RewriteRule ^/.*\.(log|ini)$ - [F,L]
above rule should block any file with extension .ini and .log
I tried adding the following rules…
The file was still available.
I tired restarting the web server after each attempt.
#1
#block any file with extension .ini and .log
RewriteRule ^/.*\.(log|ini)$ - [F,L]
#2
<Files “.user.ini”>
Require all denied
<IfModule !mod_authz_core.c>
Order deny,allow
Deny from all
#3
location ~ \.user\.ini$ {
deny all;
}
That worked can someone help get this added to the RewriteRule Template's !!
what do you mean ?
As you can see in this screenshot I am using the RewriteRule ^/.*\.(log|ini)$ - [F,L] and its not working…
When this is working you can see the RewriteRule Template’s is yellow.
<Files “.user.ini”>
Require all denied
<IfModule !mod_authz_core.c>
Order deny,allow
Deny from all
This rule also did not work.
RewriteRule ^.*\.(log|ini)$ - [F,L]
try this one.
others directive will NOT work.
It only supports rewrite rule , by rewriterule it means , only string that starts with “rewritecond” and “rewriterule”
is that OLS or enterprise ? did you restart OLS ?
I tested it worked
`
[root@test public_html]# curl -I -XGET http://xxx/test.ini
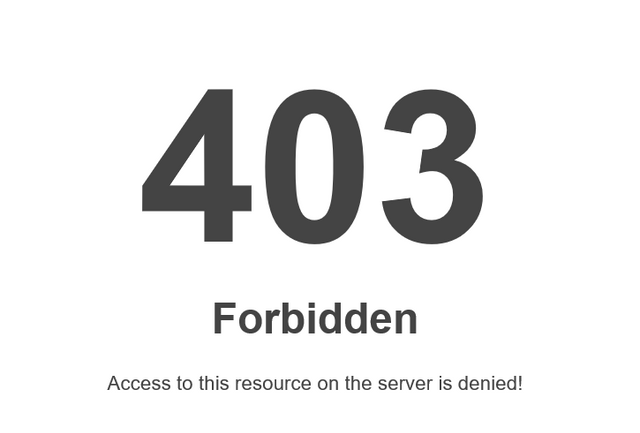
HTTP/1.1 403 Forbidden
Content-Type: text/html
Cache-Control: private, no-cache, max-age=0
Pragma: no-cache
Content-Length: 1139
Date: Thu, 29 Aug 2019 19:26:21 GMT
Server: LiteSpeed
Connection: Keep-Alive
[root@test public_html]# curl -I -XGET http://xxx/.test.ini
HTTP/1.1 403 Forbidden
Content-Type: text/html
Cache-Control: private, no-cache, max-age=0
Pragma: no-cache
Content-Length: 1139
Date: Thu, 29 Aug 2019 19:26:24 GMT
Server: LiteSpeed
Connection: Keep-Alive
[root@test public_html]# cat .htaccess
RewriteRule ^.*\.(log|ini)$ - [F,L]
`
The last one may of worked when I tried different browsers IE, Edge and Firefox… I get 403 Forbidden
As you can see the following rule is working!!!
RewriteRule ^.*\.(log|ini)$ - [F,L]
Thank You “qtwrk” !!!
Wonder if we can get this added as a template ? as shown in the first picture
for that , you need to get @usmannasir