so , after we were able to login to webadmin console , there is a lot of new advanced options for us.
for example , how to add http header to your website.
some http header , for example like HSTS is really useful nowadays.
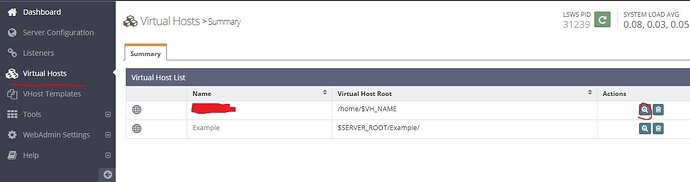
login to console , go to Virtual Hosts , and select your site, as screenshot
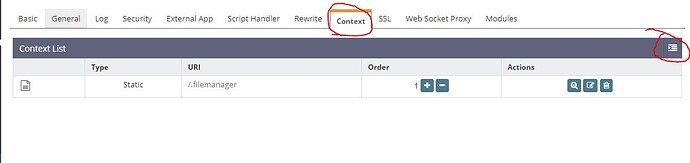
now goes to “Context” tab , click “Add” , as you can see in screenshot
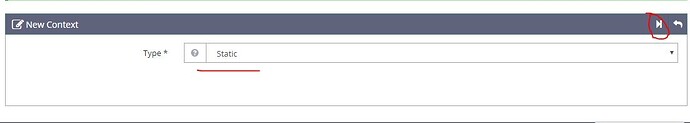
Add new context , type: Static, and click “Next”
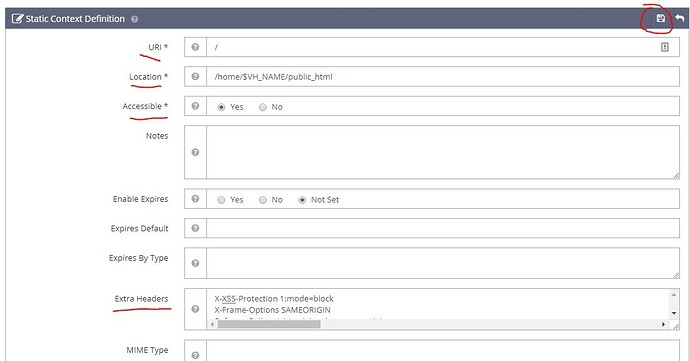
now fulfill following required options , in this case http header needs to be site-wide , so
URI: /
Location: /home/$VH_NAME/public_html
Accessible: Yes
Extra Header:
add the header you need.
since every webserver has its own syntax , so you may got it wrong first , usually you need to tweak with ; or space by adding or removing them , I will
list out some header I have confirmed working on OLS.
after added your headers , save it , and remember to restart OLS to take effect.
Examples of http header:
Content-Security-Policy default-src 'self' data: 'unsafe-eval' 'unsafe-inline' https://www.google-analytics.com https://ajax.cloudflare.com
X-XSS-Protection 1;mode=block
X-Frame-Options SAMEORIGIN
Referrer-Policy strict-origin-when-cross-origin
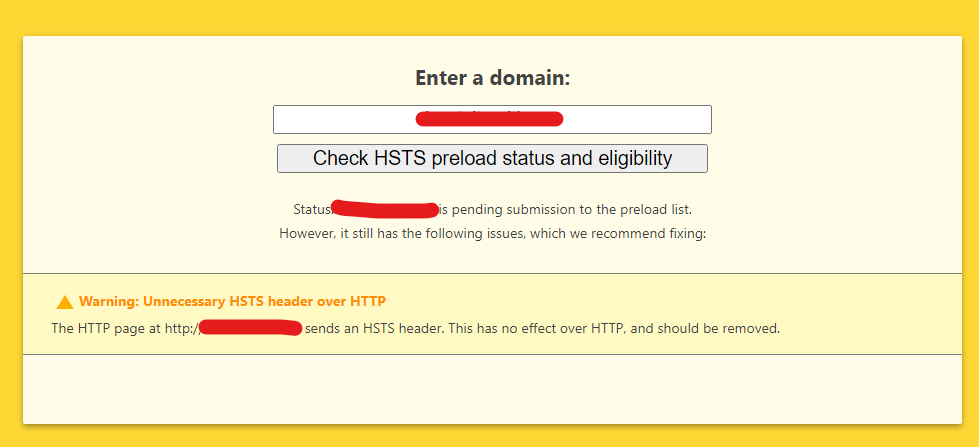
Strict-Transport-Security: max-age=15552000
X-Content-Type-Options nosniff
Public-Key-Pins 'pin-sha256="pin1"; pin-sha256="pin2"; max-age=2592000'
original posted here by myself , and translated by myself ![]()