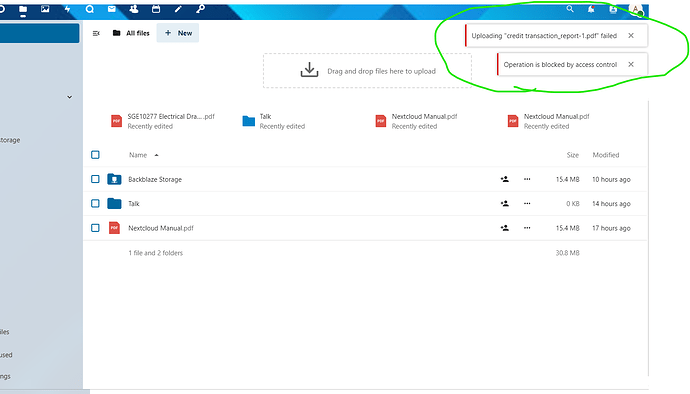
Hi All
Cyberpanel Current Version: 2.3
i recently install Nextcloud on a sub domain and everything has worked out well apart from one issue i cant upload files from a web browser, (the desktop client has no issues),
i have traced the issue down to MODSCAN but i know nothing about modscan can anyone assist if possible, if i turn modscan off it works no issues turn it back on same issue
This is the error in the nextcloud Log
BadRequest
This is the error log from cyberpanel (i cleared the log and attempted to upload file and this is the error)
2024-04-23 09:16:53.753367 [INFO] [3002] [59.100.243.150:64365-Q:0A38756CF062EA09-372#cloud.ecmind.com.au] [Module:mod_security] ModSecurity: Warning. Matched "Operator Within' with parameter |application/x-www-form-urlencoded| |multipart/form-data| |multipart/related| |text/xml| |application/xml| |application/soap+xml| |application/x-amf| |application/json| |application/cloudevents+json| (134 characters omitted)’ against variable TX:content_type' (Value: |application/pdf|’ ) [file “/usr/local/lsws/conf/modsec/owasp-modsecurity-crs-3.0-master/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf”] [line “937”] [id “920420”] [rev “”] [msg “Request content type is not allowed by policy”] [data “|application/pdf|”] [severity “2”] [ver “OWASP_CRS/3.3.2”] [maturity “0”] [accuracy “0”] [tag “application-multi”] [tag “language-multi”] [tag “platform-multi”] [tag “attack-protocol”] [tag “paranoia-level/1”] [tag “OWASP_CRS”] [tag “capec/1000/255/153”] [tag “PCI/12.1”] [hostname “cloud.ecmind.com.au”] [uri “/remote.php/dav/files/admin/transaction_report-1.pdf”] [unique_id “171382781394.789785”] [ref “o0,15v207,15t:lowercase”]Ge' with parameter 5’ against variable TX:ANOMALY_SCORE' (Value: 5’ ) [file “/usr/local/lsws/conf/modsec/owasp-modsecurity-crs-3.0-master/rules/REQUEST-949-BLOCKING-EVALUATION.conf”] [line “80”] [id “949110”] [rev “”] [msg “Inbound Anomaly Score Exceeded (Total Score: 5)”] [data “”] [severity “2”] [ver “OWASP_CRS/3.3.2”] [maturity “0”] [accuracy “0”] [tag “application-multi”] [tag “language-multi”] [tag “platform-multi”] [tag “attack-generic”] [hostname “cloud.ecmind.com.au”] [uri “/remote.php/dav/files/admin/transaction_report-1.pdf”] [unique_id “171382781394.789785”] [ref “”]
thank you for your assistance
So i found some rules that have worked but do i need to do this for every file type
SecRule REQUEST_HEADERS:Content-Type “@rx image/jpeg” @rx application/pdf” @rx application/vnd.ms-excel” @rx image/png” @rx application/vnd.openxmlformats-officedocument.wordprocessingml.document”
DanielCollins:
This is the error log from cyberpanel (i cleared the log and attempted to upload file and this is the error)
2024-04-23 09:16:53.753367 [INFO] [3002] [59.100.243.150:64365-Q:0A38756CF062EA09-372#cloud.ecmind.com.au] [Module:mod_security] ModSecurity: Warning. Matched "Operator Within' with parameter |application/x-www-form-urlencoded| |multipart/form-data| |multipart/related| |text/xml| |application/xml| |application/soap+xml| |application/x-amf| |application/json| |application/cloudevents+json| (134 characters omitted)’ against variable TX:content_type' (Value: |application/pdf|’ ) [file “/usr/local/lsws/conf/modsec/owasp-modsecurity-crs-3.0-master/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf”] [line “937”] [id “920420”] [rev “”] [msg “Request content type is not allowed by policy”] [data “|application/pdf|”] [severity “2”] [ver “OWASP_CRS/3.3.2”] [maturity “0”] [accuracy “0”] [tag “application-multi”] [tag “language-multi”] [tag “platform-multi”] [tag “attack-protocol”] [tag “paranoia-level/1”] [tag “OWASP_CRS”] [tag “capec/1000/255/153”] [tag “PCI/12.1”] [hostname “cloud.ecmind.com.au”] [uri “/remote.php/dav/files/admin/transaction_report-1.pdf”] [unique_id “171382781394.789785”] [ref “o0,15v207,15t:lowercase”]Ge' with parameter 5’ against variable TX:ANOMALY_SCORE' (Value: 5’ ) [file “/usr/local/lsws/conf/modsec/owasp-modsecurity-crs-3.0-master/rules/REQUEST-949-BLOCKING-EVALUATION.conf”] [line “80”] [id “949110”] [rev “”] [msg “Inbound Anomaly Score Exceeded (Total Score: 5)”] [data “”] [severity “2”] [ver “OWASP_CRS/3.3.2”] [maturity “0”] [accuracy “0”] [tag “application-multi”] [tag “language-multi”] [tag “platform-multi”] [tag “attack-generic”] [hostname “cloud.ecmind.com.au”] [uri “/remote.php/dav/files/admin/transaction_report-1.pdf”] [unique_id “171382781394.789785”] [ref “”]
thank you for your assistance
Try this rules.
PS: I am not very good with ModSec rules
SecRule REQUEST_FILENAME "@beginsWith /remote.php/dav/files/admin/" \
"id:1001,\
phase:1,\
pass,\
nolog,\
ctl:requestBodyAccess=On"
SecRule REQUEST_HEADERS:Content-Type "!@rx (?:multipart\/form-data)|(?:application\/x-www-form-urlencoded)" \
"id:1002,\
phase:1,\
pass,\
nolog,\
ctl:requestBodyAccess=On"
usmannasir:
SecRule REQUEST_FILENAME "@beginsWith /remote.php/dav/files/admin/" \
"id:1001,\
phase:1,\
pass,\
nolog,\
ctl:requestBodyAccess=On"
Cheers the first rule looks like it’s for the admin user if there is another user I’d have to add in another rule yeah.
Or do you I think I can drop the /admin/ and it will work with allusers because the rule is @bedinsWith
Also what the secoud rule do. That really doesn’t make sense to me lol
Yes try removing admin from username.
Second rule checks the Content-Type header of the request. If it doesn’t match the regular expression (?:multipart\/form-data)|(?:application\/x-www-form-urlencoded), which are common content types for file uploads, it enables access to the request body.
these rules didnt work@beginsWith /remote.php/dav/files/admin/”
SecRule REQUEST_HEADERS:Content-Type “!@rx (?:multipart/form-data)|(?:application/x-www-form-urlencoded)”
Maybe try in OpenLiteSpeed or ModSec community.
Didn’t realise there was a modsec community lol. Cheers thanks for your help.
I’m running with all the rules I have set up at the moment and it seems to have no issues. I’ll just remember how to add them if another item comes up.
I’ll post somthing back here if I get an answer from elsewhere.
1 Like