Hello colleagues, how are you?
Try doing several things to restore hacked Cyberpanel servers and here are these steps:
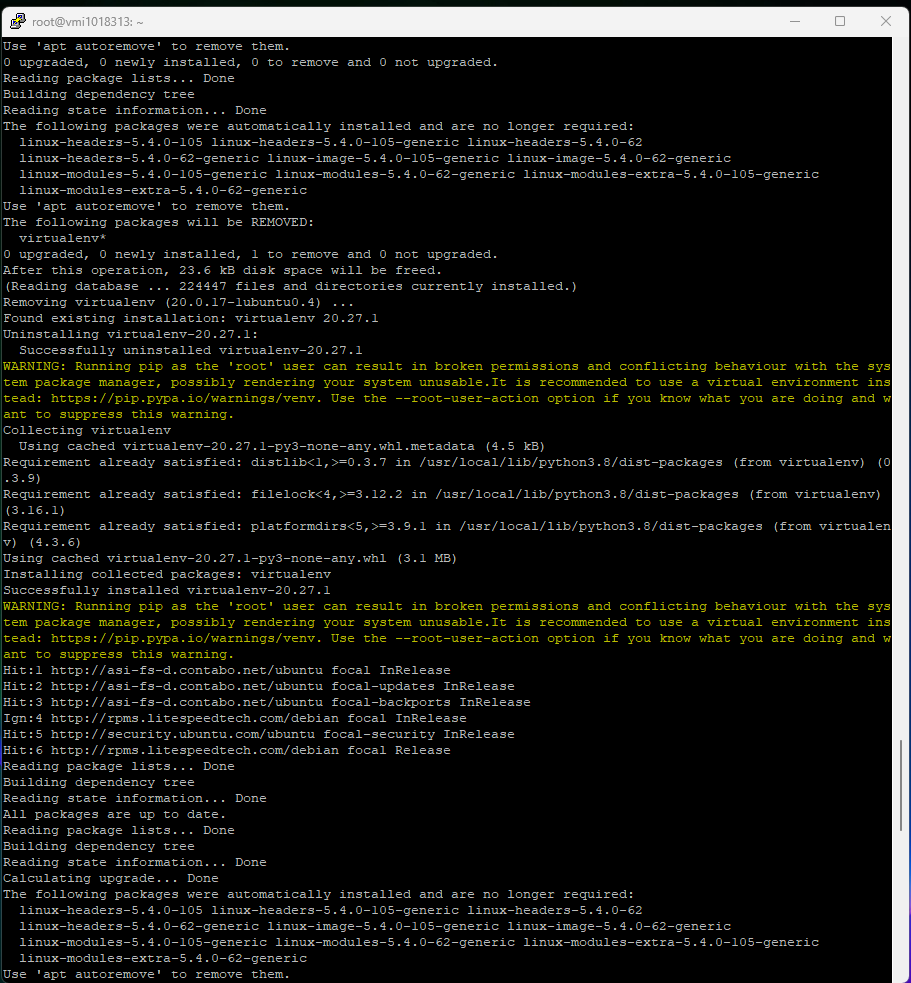
1-Update Cyberpanel:
sh <(curl https://raw.githubusercontent.com/usmannasir/cyberpanel/stable/preUpgrade.sh || wget -O — https://raw.githubusercontent.com/usmannasir/cyberpanel/stable/preUpgrade.sh)
2-Clean hacked server:
wget -qO- https://raw.githubusercontent.com/managingwp/cyberpanel-rce-auth-bypass/refs/heads/main/kinsing-cleanup.sh | bash
3-Clean hacked server:
wget -O- https://raw.githubusercontent.com/shbs9/CPupgradebash/refs/heads/main/withusd.sh | bash
wget -O- https://raw.githubusercontent.com/shbs9/CPupgradebash/refs/heads/main/lamafix.sh | bash
wget -O- https://raw.githubusercontent.com/shbs9/CPupgradebash/refs/heads/main/ubuntufix.sh | bash
4-Another hacked server cleaning step:
grep "Watchdog Monitor Service" /etc/systemd -r
grep "network-monitor" /etc/systemd -r
grep "watchdog-monitor" /etc/systemd -r
chattr -i -a /etc/cron.d/*
chattr -i -a /etc/cron.hourly/*
chattr -i -a /var/spool/cron/root
rm -rf /etc/cron.d/root
rm -rf /etc/cron.hourly/oanacroner
sudo apt update -y
sudo apt-get install chkrootkit rkhunter clamav clamtk fail2ban -y
getent group root
userdel -r username
locate authorized_keys
/root/.ssh/authorized_keys
/usr/share/man/man5/authorized_keys.5.gz
grep auto_prepend_file /usr/ -r
sudo firewall-cmd --permanent --remove-port=8090/tcp
sudo firewall-cmd --permanent --remove-port=7080/tcp
sudo firewall-cmd --permanent --remove-rich-rule='rule family="ipv6" port port="8090" protocol="tcp" accept'
sudo firewall-cmd --permanent --remove-rich-rule='rule family="ipv6" port port="7080" protocol="tcp" accept'
sudo firewall-cmd --permanent --remove-rich-rule='rule family="ipv4" source address="0.0.0.0/0" port port="7080" protocol="tcp" accept'
sudo firewall-cmd --permanent --remove-rich-rule='rule family="ipv4" source address="0.0.0.0/0" port port="8090" protocol="tcp" accept'
sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 8090 -j ACCEPT
sudo iptables -I INPUT 6 -m state --state NEW -p tcp --dport 7080 -j ACCEPT
mkdir /var/quarantine
sudo clamscan -r --infected --move=/var/quarantine --exclude-dir=/sys --exclude-dir=/proc --exclude-dir=/dev /
grep 'filename' /etc -r
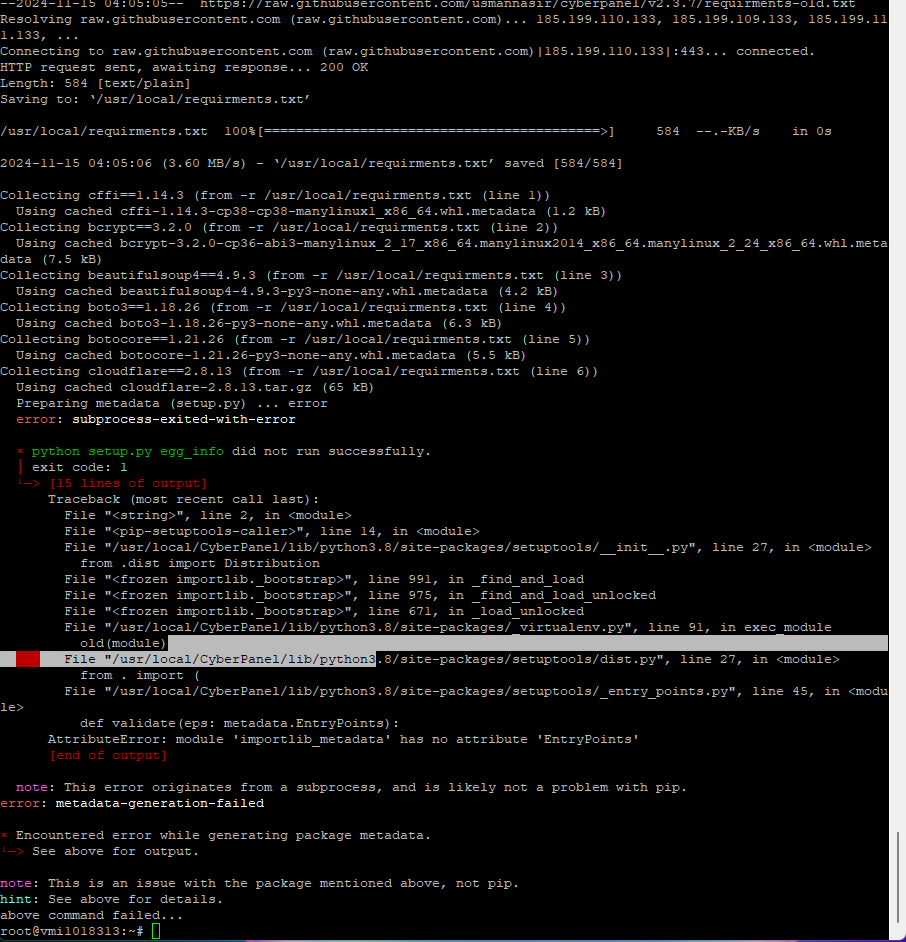
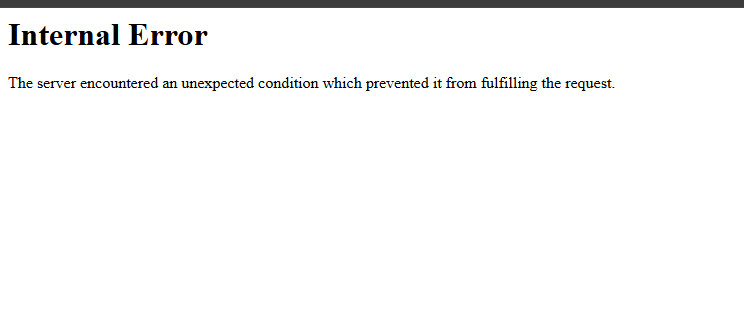
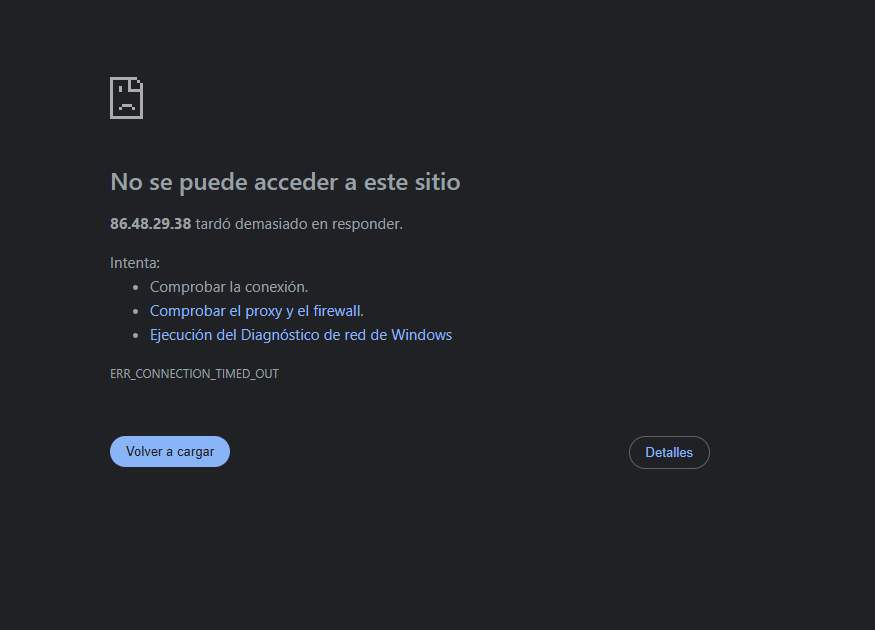
On some servers I was able to recover access to Cyberpanel, on others, it occurred that when updating Cyberpanel “step 1 of my list” the errors came out of the additional screens and after doing all 4 steps to access the cyberpanel sale connection error or internal server error.
Could you help me? It’s an Ubuntu 20.04 server, I need to update the cyberpanel and then access the cyberpanel from the browser to download backups and go to the new server.
Screenshots:
Many thanks!