Here is the solution to change the default CyberPanel accounts username.
[Which should always and must be the default action after deploying a CyberPanel instance for minimum security]
After first time login to CyberPanel using the admin username, create a new admin user account with a username of your choosing and security set to high.
Now logout and login using this newly created account.
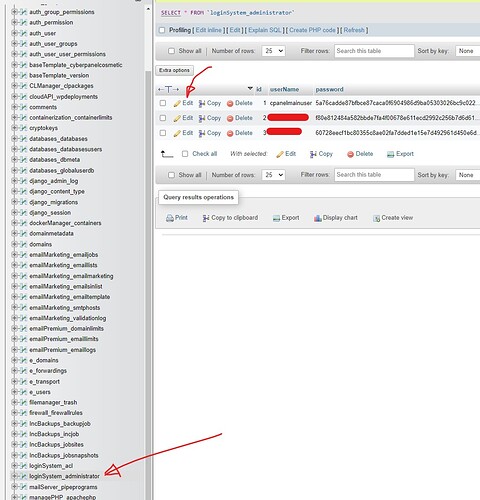
Then access cyberpanel database through PHPMYAdmin, and find the loginSystem_administrator table.
There you simply click edit on that row with id 1 and username admin, and change the admin username to any arbitrary username to help mitigate brute force attempts [you never should need this username to login again].
Once username has been modified to anything else but admin, just click go and logout.
Now you should be able to login to CyberPanel using this new username, if ever needed [but you should never use this system admin account with ID 1 to login through cyberpanel ever again]
should you loose access to the cyberpanel, forgetting the username, you can always just get the list of users to reveal usernames or create a new admin user using the CyberPanel CLI commands through SSH terminal access as listed here
like so, to list users:
cyberpanel listUsers
and like so to create an admin user:
cyberpanel createUser --firstName Cyber --lastName Panel --email [email protected] --userName cyberpanel --password securepassword --websitesLimit 10 --selectedACL user --securityLevel HIGH
Final words:
Of course go ahead and turn on the new awesome 2FA on all users, to further increase security.
And I know it’s tempting to to just delete or suspend the default ‘admin’ user with ID 1 in the database, but trust me that will likely create a bunch of other issues as that ID is attached to a lot of website instance permissions, and will likely break your websites.